HTB Cyber Apocalypse 2023 - (Hardware) Debug
‘Debug’ was one of the challenges in the ‘Hardware’ category at HTB’s Cyber Apocalypse 2023.
Its difficulty was ‘Easy’ and it involved UART signals captured by a logic analyzer.
We got a single file for this challenge: hw_debug.sal.
I already knew about the .sal extension from the previous challenge so I opened the file in Logic2 right away.
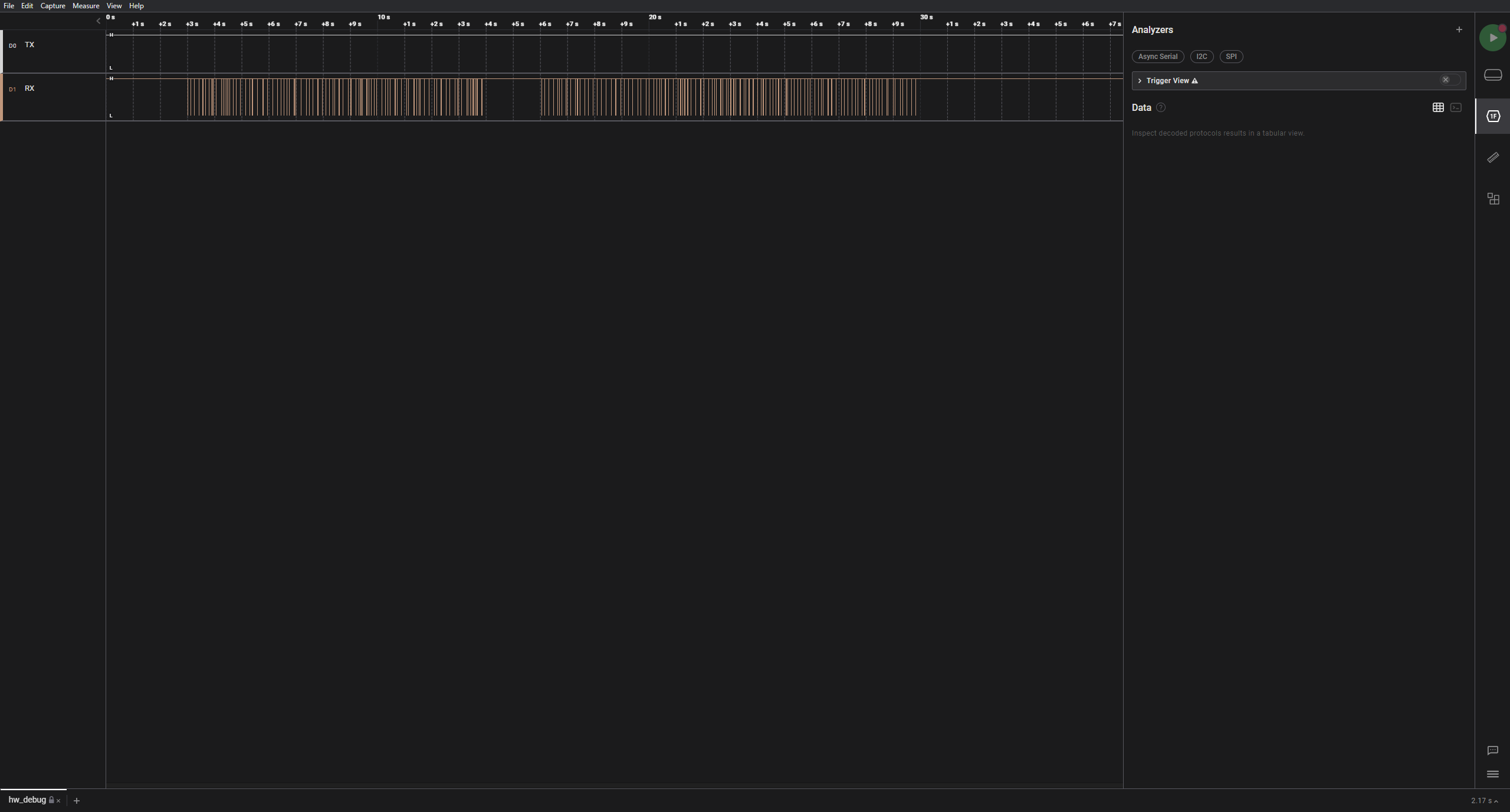
There are two visible signals: TX and RX. We can quickly see that only RX has any kind of activity.
First, I tried adding an Async Serial analyzer from Logic2 to see if I can decode any of the data transferred there.
I tried the standard baud rates: 1200, 2400, 4800, 9600, 19200, 38400, 57600, and 115200.
115200 seemed to be the one that worked.
Now Logic2 also displays data that seems to be valid.
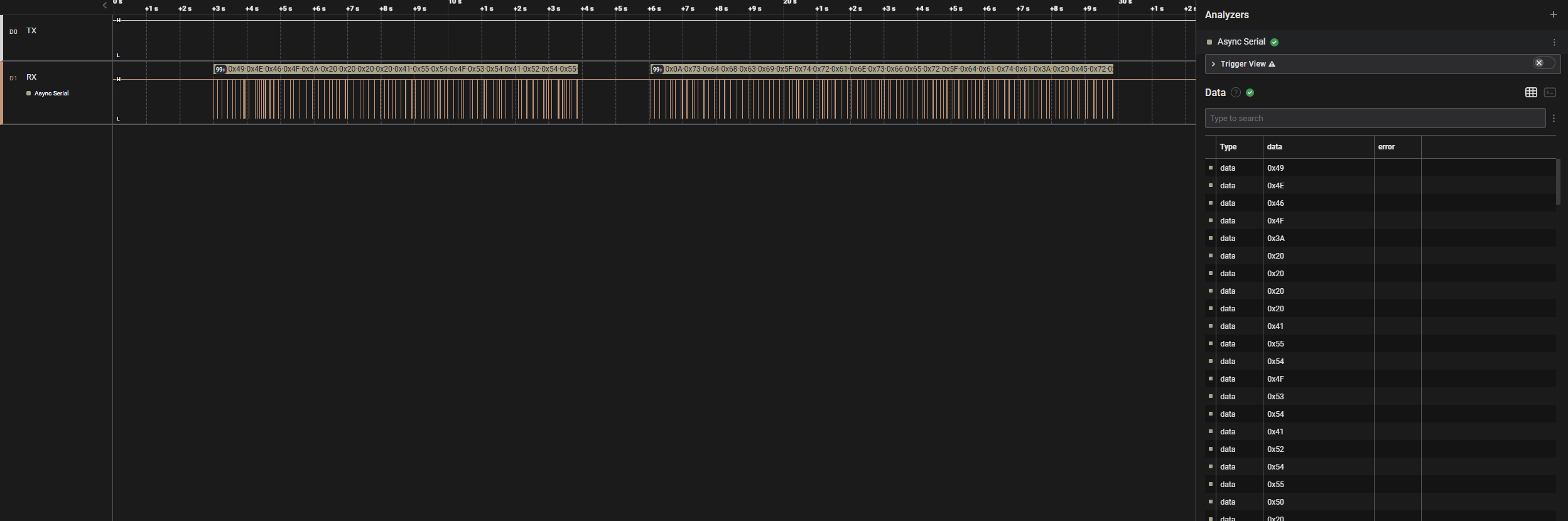
I export that and get/copy those hex bytes that were transferred.
Then, I put them in CyberChef and use the ‘From Hex’ operation.
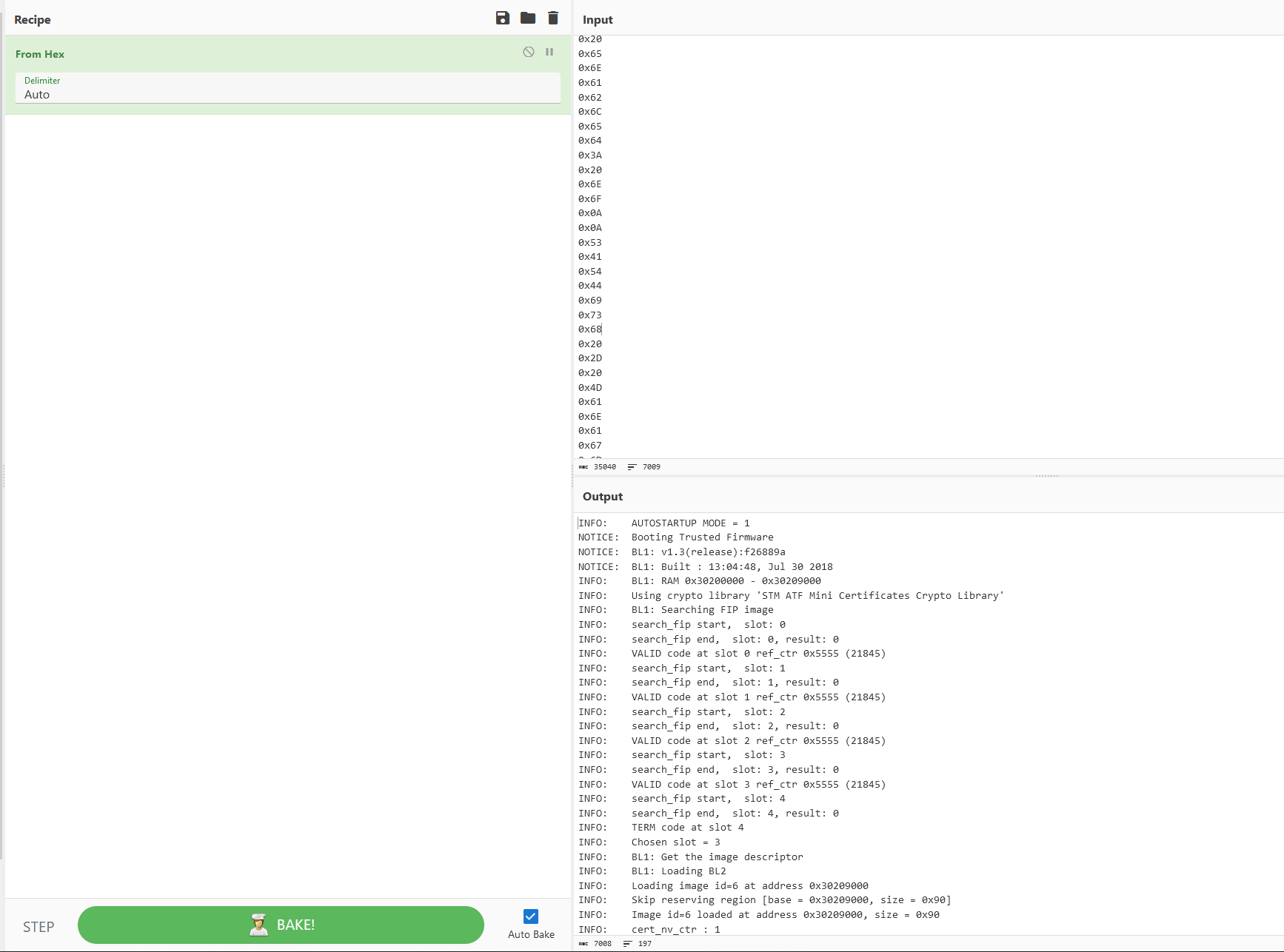
This seems to be the output of a debug shell.
Let’s take a look at what is written to that shell.
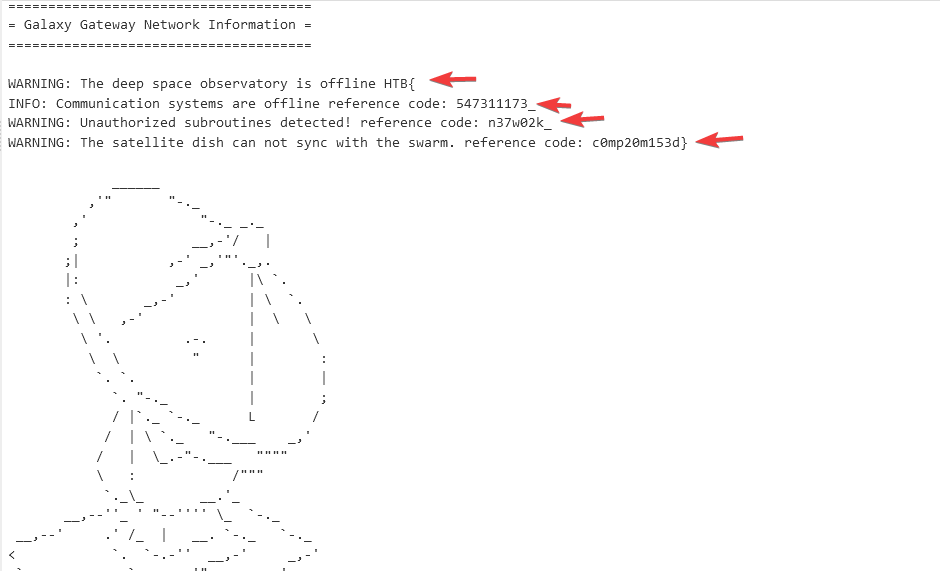
At the end of the boot sequence, the device prints the flag in multiple lines and then asks the user to login (over UART, probably).
We put the pieces of that flag together and we have our flag: HTB{547311173_n37w02k_c0mp20m153d}
More hardware challenges
These are the other hardware challenges from this CTF
- Hardware 1/5 - Very Easy - Critical Flight
- Hardware 2/5 - Very Easy - Timed Transmission
- Hardware 3/5 - Easy - Debug (you are here)
- Hardware 4/5 - Easy - Secret Code
- Hardware 5/5 - Medium - HM74