TenableCTF 2022 OSINT Challenges Writeup
Find me if you can
The hint for this challenge was made of these two images (the first one was a originally gif):

The second one is quite a clear reference to the recent “4shell” vulnerabilities (mainly Log4Shell & Spring4Shell).
So based on the first image, it’s more likely to be about Spring4Shell because the image contains … springs.
The “spring” part took me way too long to figure (It was actually pointed out by someone else from our team) as I was trying to come up with solutions that involved social media (commonly seen in OSINT challenges).
However, once you made the connection with Spring4Shell you can try to do a Google search for “Spring4Shell Tenable” and among the first results you will probably find Tenable’s blogpost about the exploit.
This is the article:
https://www.tenable.com/blog/spring4shell-faq-spring-framework-remote-code-execution-vulnerability
And if you look at the source code for that page you will spot that the flag is hidden in there.
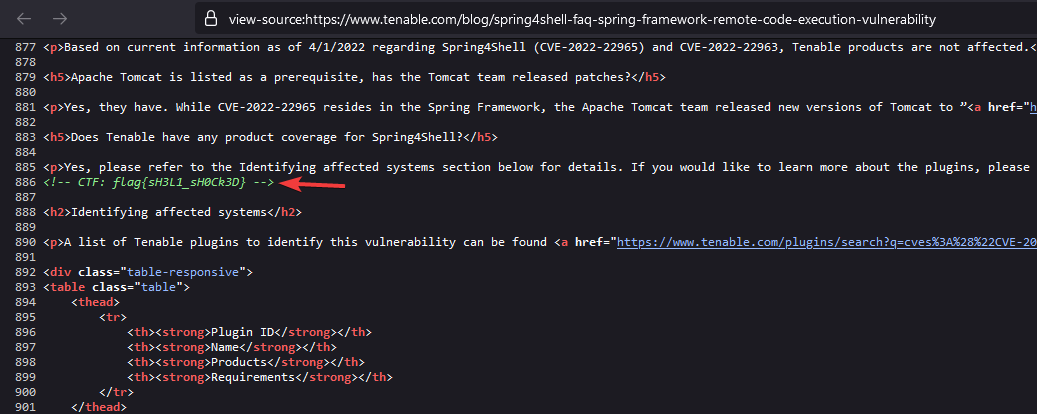
Can you dig it?
The hint for the second challenge was this image:

The main hint is probably something to do with “zero clicks” (as in, a zero-click exploit).
Other hints/keywords that might be derived from this image might be: three and skulls. Not sure if there’s any recent exploit that relates to those.
So first, we try using the same method as the last challenge and we search for “zero click” on Tenable’s website.
We go through the results and search for “flag{“ in the page’s source code.
After a few tries we get to the following article that has the flag hidden in it:
https://www.tenable.com/blog/cve-2022-30190-zero-click-zero-day-in-msdt-exploited-in-the-wild
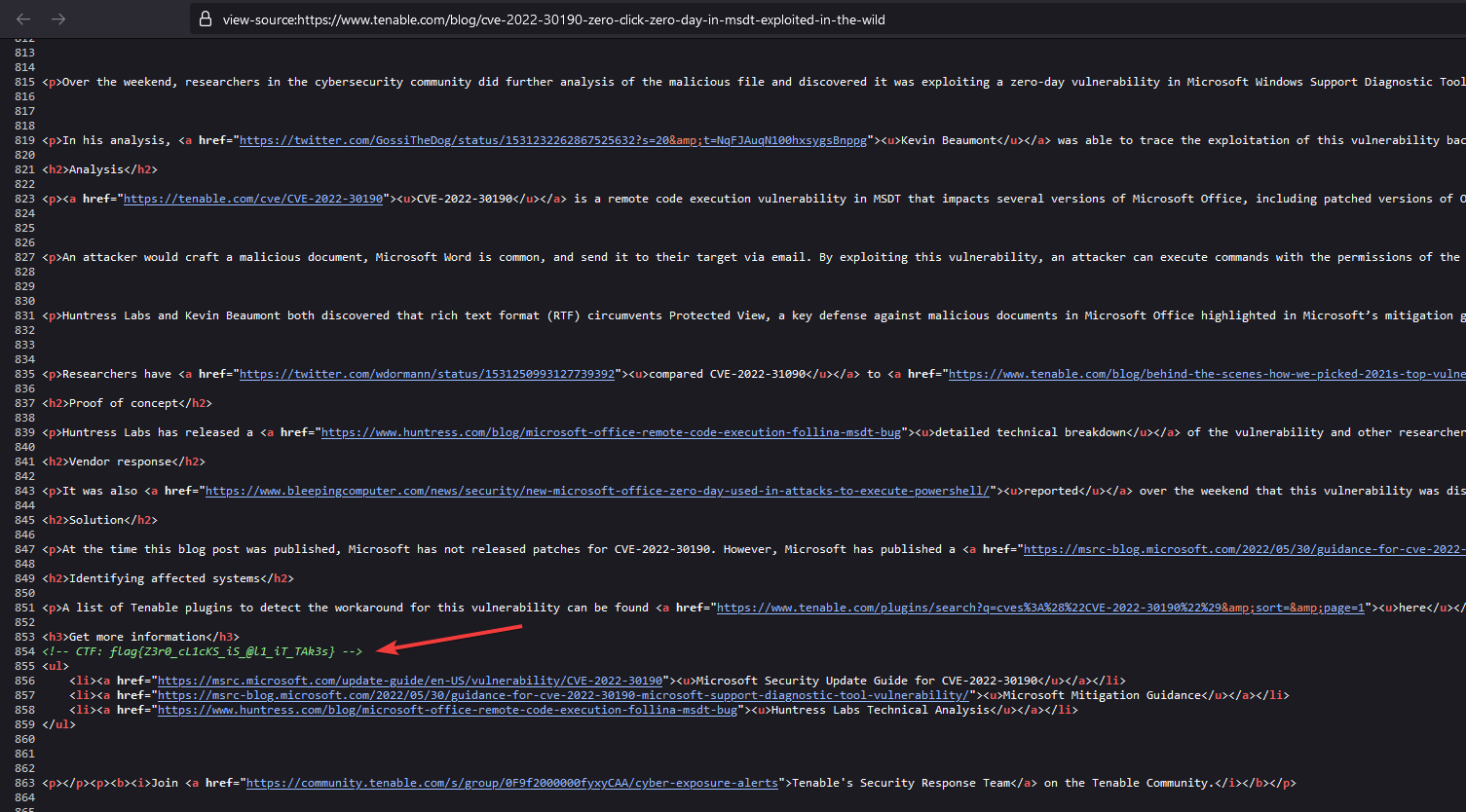
Lets network
The hint for the third challenge was made of these two images:
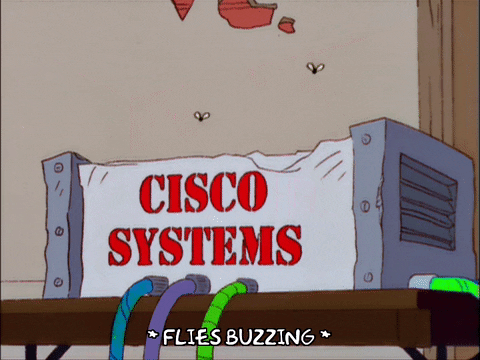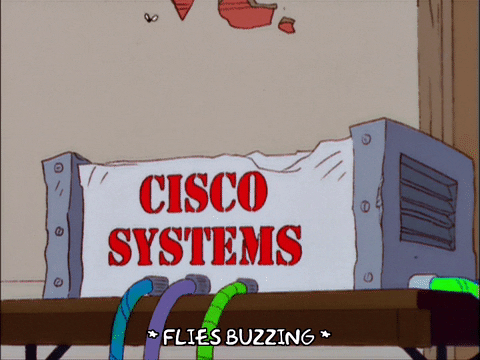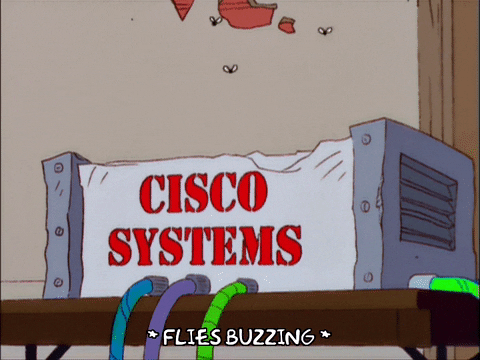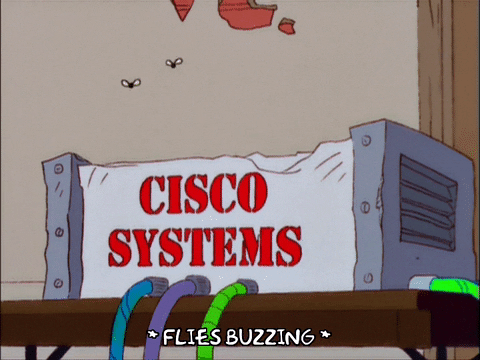

So the main hint is Cisco RV. That’s a series of routers made by Cisco.
Keeping the trend from the previous challenges, we search for “Cisco RV” in their vulnerability database.
Among the first results we can find this page:
https://www.tenable.com/blog/cve-2022-20699-cve-2022-20700-cve-2022-20708-critical-flaws-in-cisco-small-business-rv-series
Which had the flag embedded in it.
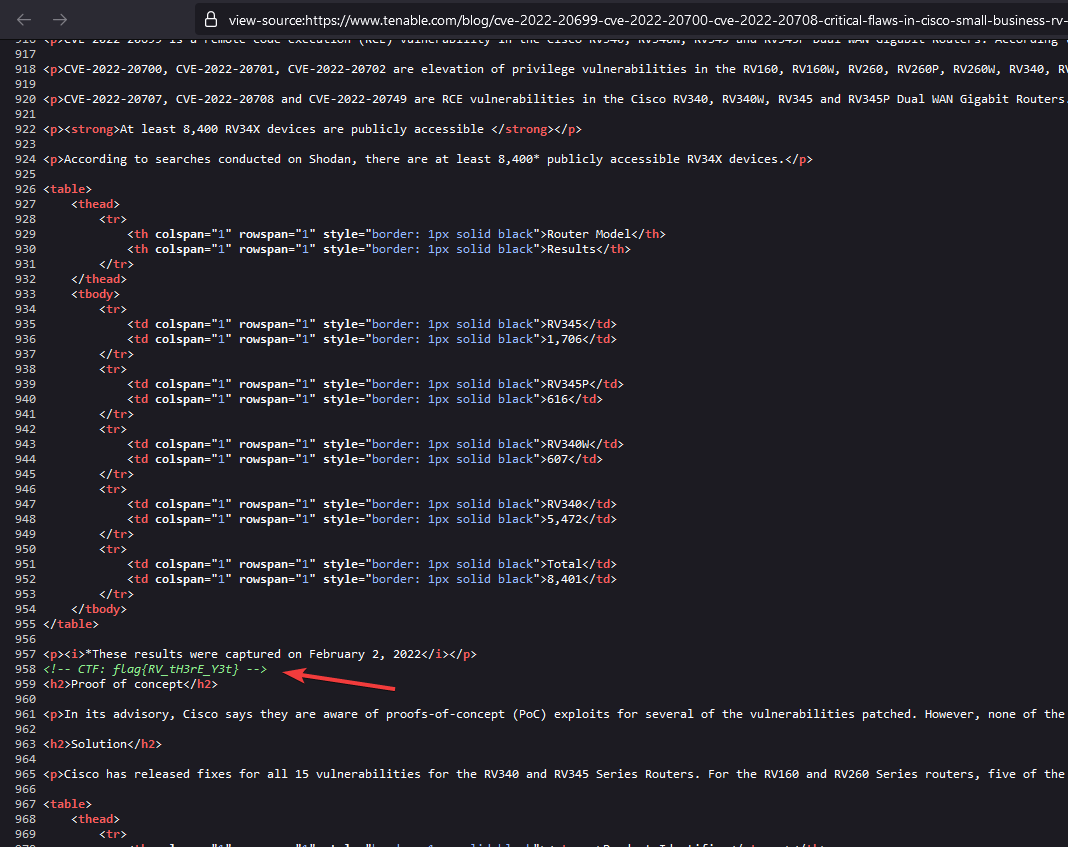
Another way of solving this
Those three flags weren’t hard to find after we made the connection with Tenable’s vulnerability database.
Howver, there is a different method of obtaining these flags.
Tenable’s search feature looks at the code that isn’t rendered too.
So one could search for “flag{“ and get the three pages that contained flags as results:
https://www.tenable.com/blog/search?field_blog_section_tid=All&combine=flag%7B
This might not work anymore when you are reading it; the flags could be removed. However, it looked something like this.
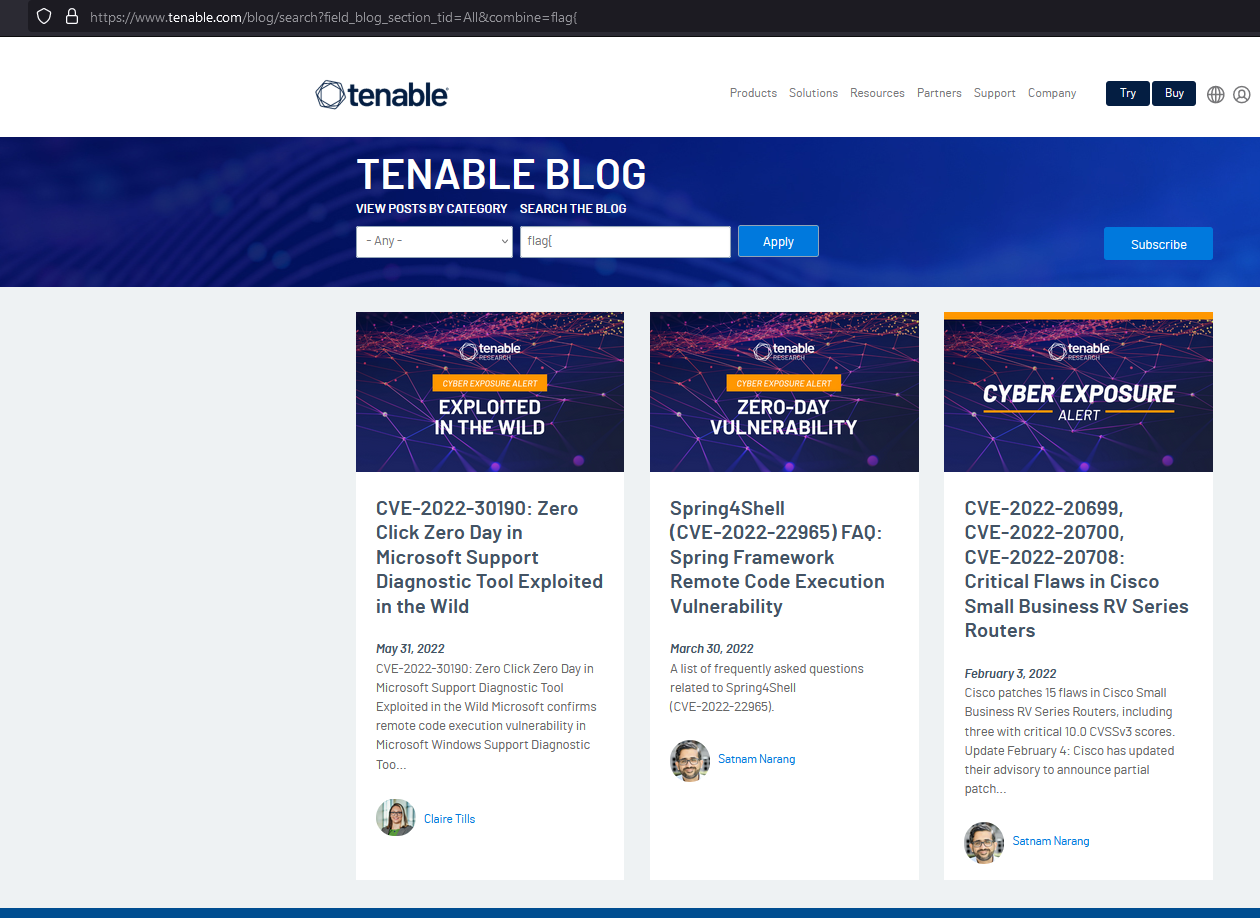
We only came up with this idea after the CTF was over but this was an interesting and probably unintended way of solving this challenge.