HTB Business CTF 2025 - Echoes of Authority writeup
Echoes of Authority was a challenge at the HTB Business CTF 2025 (Global Cyber Skills Benchmark CTF 2025) from the ‘Hardware’ category.
For this challenge, we got a PCAP file.
For me, this was an interesting challenge because it was the first time I had to analyze RTP using wireshark. There’s also another protocol that I knew about that I was able to use.
The main thing that we notice when opening it using Wireshark is that almost all the traffic is RTP, a protocol used for video and audio streams.
We can go in Telephony->RTP->RTP Player and listen to this stream.
It contains a message informing the caller they need to insert an 8-digit code followed by the hash sign (#).
I would expect to hear the beeps from the keys being pressed but it looks like those aren’t part of this stream.
The gap can even be seen on the waveform.
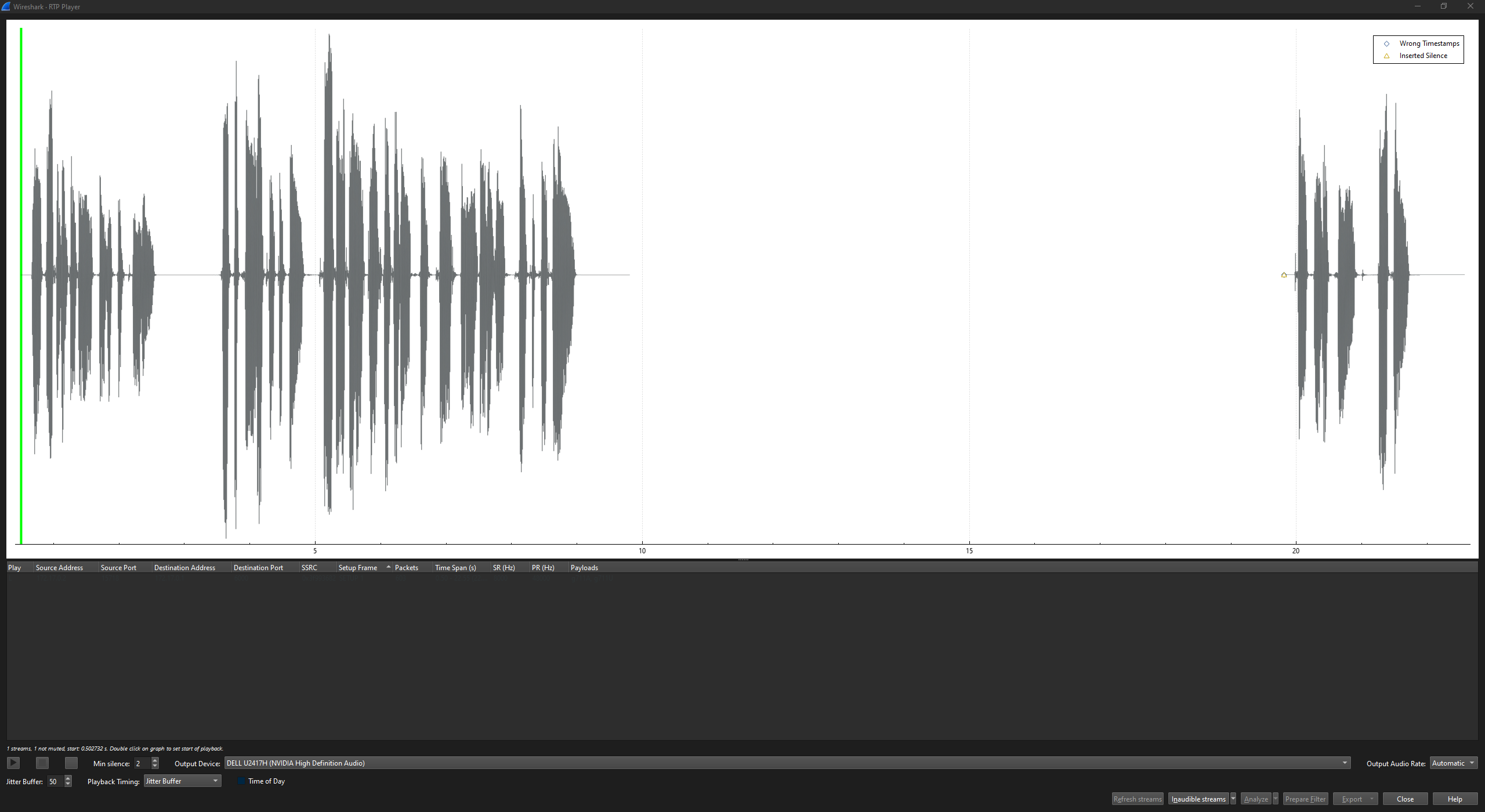
After that gap, the caller is informed that their code was correct and thus they are granted access.
Also, based on the challenge’s text, we have to retrieve the code. The flag will be HTB{<8-digit-code>}
If I use the same menu but go to ‘RTP Streams’ (Telephony->RTP->RTP Streams) I can see that we have 2 different streams.
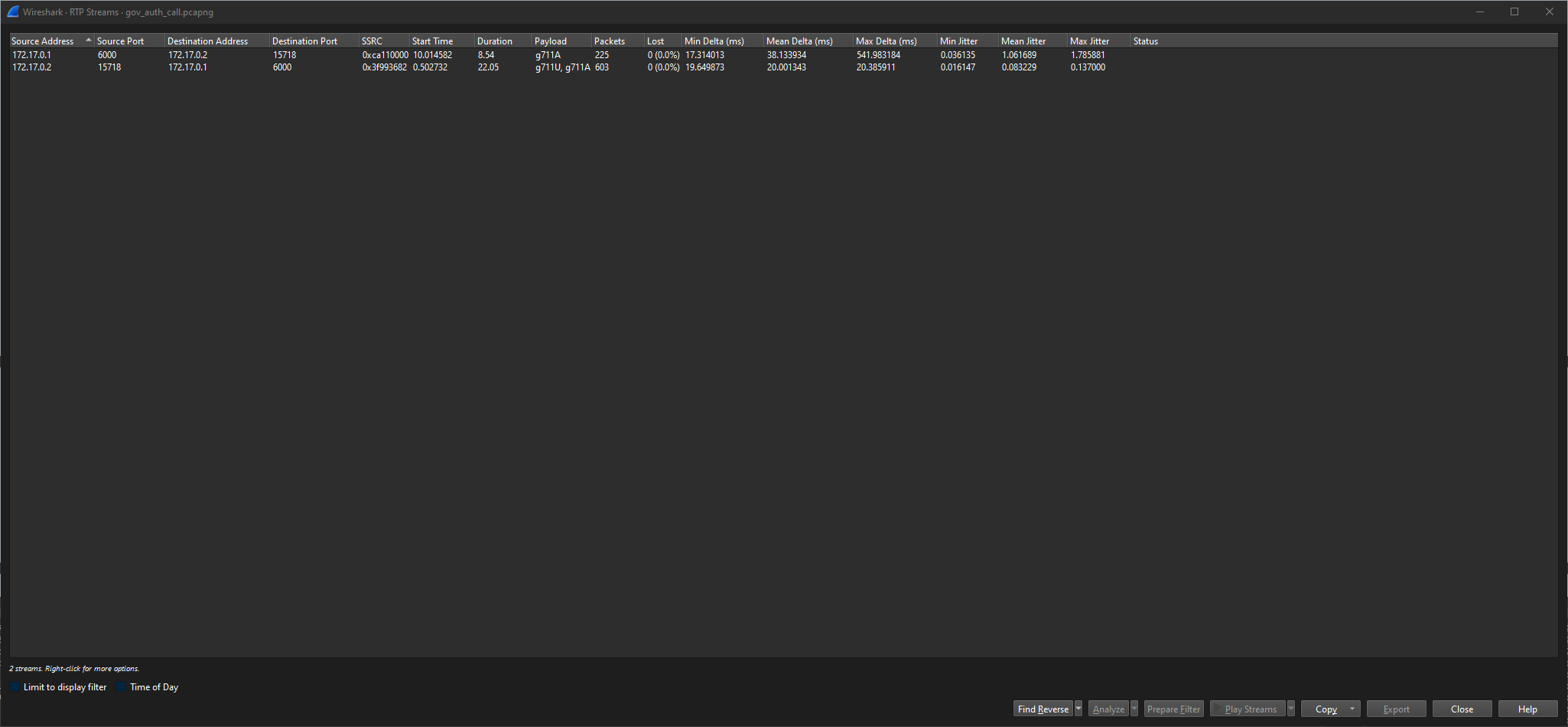
Playing the shorter one has the beeps I would expect to hear when someone is pressing keys on their phone.
I knew about these beeps: they are used to send the key being pressed on one end of the call to the other end of the call. That’s how those services asking you to press a certain key to select things from a menu work (think of what you get when calling customer service)
After a bit of googling, I learned that this is called Dual-tone multi-frequency (DTML) signaling: https://en.wikipedia.org/wiki/DTMF_signaling
And I also found tools that can decode these tones. Tools like this one: https://dtmf.netlify.app/
The very first attempt (default settings) has some numbers being repeated: You can see that the 1 from the first digit also gets into the second one.
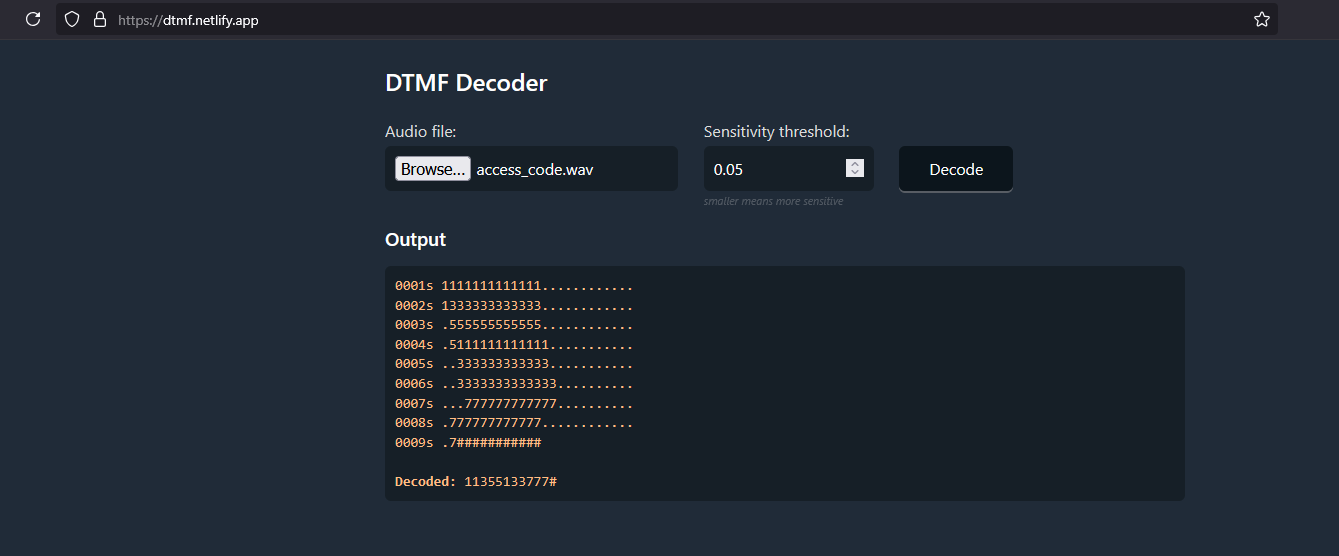
But the tool also allows us to set different sensitivity thresholds and I did that to get a single number on every line.
This time the code (and the hash sign too) can be easily seen: 13513377.
So the flag for this challenge is: HTB{13513377}